Tấn công DoS là một kiểu tấn công mà một người làm cho một
hệ thống không thể sử dụng, hoặc làm cho hệ thống đó chậm đi một cách đáng kể với
người dùng bình thường, bằng cách làm quá tải tài nguyên của hệ thống. Nếu kẻ tấn
công không có khả năng thâm nhập được vào hệ thống, thì chúng cố gắng tìm cách
làm cho hệ thống đó sụp đổ và không có khả năng phục vụ người dùng bình thường
đó là tấn công Denial of Service (DoS). Mặc dù tấn công DoS không có khả năng
truy cập vào dữ liệu thực của hệ thống nhưng nó có thể làm gián đoạn các dịch vụ
mà hệ thống đó cung cấp.Tấn công DoS là kiểu tấn công vô cùng nguy hiểm cho nên
phải có biện pháp phòng chống cho kiểu tấn công này.Sau đây mình xin hướng dẫn
cấu hình phòng chống DoS và IPS Signature trên tường lửa Fortigate 5.2
Bước 1: Các bạn vào System--> Feature Select, mở tính năng Intrustion Protection rồi chọn apply như hình bên dưới :
Bước 1: Các bạn vào System--> Feature Select, mở tính năng Intrustion Protection rồi chọn apply như hình bên dưới :
Bước 2: Các bạn vào security Profiles-->Intrustion Protection-->Turn on các Rate based Signatures
Bước 3: Ở mục Pattern Based Signatures and Filters các bạn chọn và edit và block các signatures rồi chọn ok
Bước 4: Add IPS vào policy mà mình muốn thực thi:
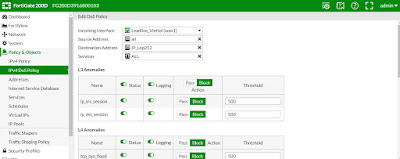
Bước 5: Tạo rule để ngăn chặn tấn công Dos . Các bạn vào mục Policy & Objects--> IPV4 Dos Policy > Create New và làm theo như hình bên dưới :
Bước 6: Các bạn có thể xem kết quả ở mục: Fortiview-->Threats để xem kết quả.
Như vậy các bạn đã hoàn thành cấu hình IPS/Dos trên Firewall Fortigate